Benefits
- Implement key requirements for know-how protection reliably throughout the entire company
- Take advantage of the possibilities offered by a particularly powerful and dynamic rights system
- Ensure validity with project roles and support collaboration at the same time

Securely implement key requirements for know-how protection throughout the entire company
Effective data protection requires an integrated approach in research and development departments as well as manufacturing and service. Implementation is performed with CONTACT Elements Roles & Access Rights via central server elements and policies that control and log access to the data over the entire lifecycle of a product or project. These access rules can be defined and maintained easily and effectively. This allows you to take full advantage of the potential offered by complete, up-to-date data for global collaboration.

Effective data protection requires an integrated approach in research and development departments as well as manufacturing and service. Implementation is performed with CONTACT Elements Roles & Access Rights via central server elements and policies that control and log access to the data over the entire lifecycle of a product or project. These access rules can be defined and maintained easily and effectively. This allows you to take full advantage of the potential offered by complete, up-to-date data for global collaboration.
Take advantage of the possibilities offered by a particularly powerful and dynamic rights system
CONTACT Elements reliably ensures the protection of sensitive data with automated procedures. The properties of a document or component such as confidentiality, maturity level or product class automatically determine the appropriate protection class. Thanks to a dynamic predicate-driven rights system, this holds true even if their values change.

CONTACT Elements reliably ensures the protection of sensitive data with automated procedures. The properties of a document or component such as confidentiality, maturity level or product class automatically determine the appropriate protection class. Thanks to a dynamic predicate-driven rights system, this holds true even if their values change.
Ensure validity with project roles and support collaboration at the same time
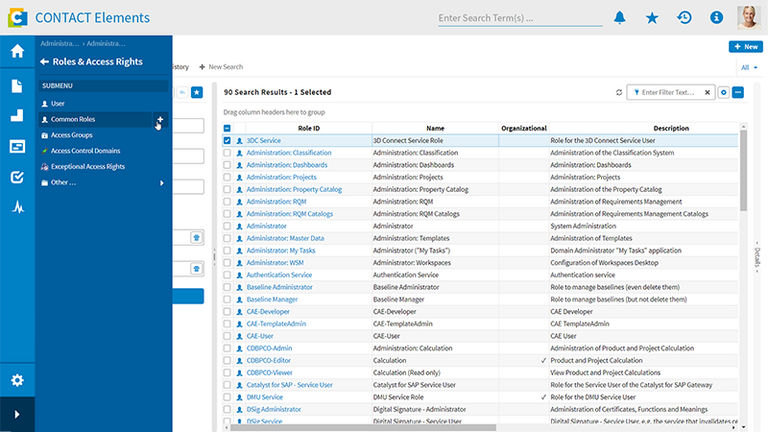
It may be that an employee changes the organizational unit they belong to, such as a project, a location or a department. In this case, instead of having to intervene manually, the dynamic permissions system will again automatically assign the appropriate permissions based on the roles and permissions specifically defined for the unit in question. This means that project and/or location-specific permissions for project managers, design engineers or quality management can be assigned automatically.
Ensure validity with project roles and support collaboration at the same time
It may be that an employee changes the organizational unit they belong to, such as a project, a location or a department. In this case, instead of having to intervene manually, the dynamic permissions system will again automatically assign the appropriate permissions based on the roles and permissions specifically defined for the unit in question. This means that project and/or location-specific permissions for project managers, design engineers or quality management can be assigned automatically.
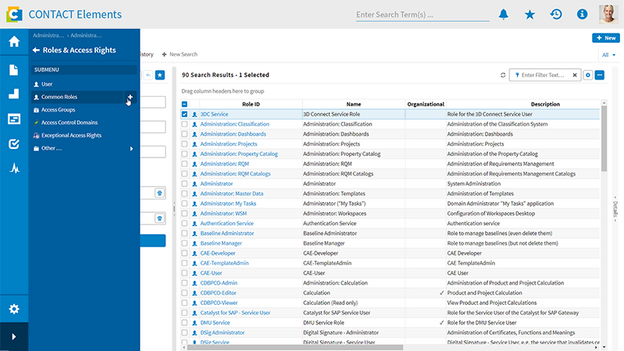
It may be that an employee changes the organizational unit they belong to, such as a project, a location or a department. In this case, instead of having to intervene manually, the dynamic permissions system will again automatically assign the appropriate permissions based on the roles and permissions specifically defined for the unit in question. This means that project and/or location-specific permissions for project managers, design engineers or quality management can be assigned automatically.
Related Elements
Know-how protection and reliable operation through secure log-in procedures, system protocols and encryption
Rely on maximum security standards with a system that is immediately adapted to the latest findings on new vulnerabilities
Ensure reliable transport encryption with fully HTTPS-based communication
Rely on access protection with personalized logins and multi-factor authentication
Ensure the confidentiality, authenticity and integrity of your data through a combination of encryption methods
Verify documents and complex PLM objects faster and meet regulatory requirements
Speed up circulation procedures for verification and approval processes
Meet regulatory requirements and improve validity control and process reliability
Intelligent Document logistics: organizing and utilizing know-how enterprise wide
Make all important documents
available on every workstation
Save valuable time when searching
for documents
Protect valuable know-how
Speed up test and release
processes
Comply with regulatory requirements
much more easily
Further information
Would you like to learn more about this topic? Choose from one of the following information offers.

